Penetration Testing
Building on results of automated and vetted scanning, a manual penetration test utilizes the same approach, techniques, attack vectors, and known vulnerabilities, but with added creativity and skills of a human-based attacker. Very few “false positive” outputs come from this step, due to the human operator understanding if they have been able to achieve a valuable attack
Penetration Testing, also known as “pen testing,” is a form of security testing that involves simulating a real-world attack on a system to identify vulnerabilities and potential exploits. The goal of penetration testing is to assess the security posture of a web and mobile application and to identify any weaknesses that could be exploited by an attacker. The penetration tester attempts to exploit vulnerabilities, typically using a combination of automated and manual techniques, to gain access to sensitive data or functionality within the application. The testing is typically conducted in a controlled environment, such as a test or staging environment, to prevent any unintended impact on the production system.
.png)
During a penetration testing engagement, the tester attempts to identify and exploit vulnerabilities in the application, using a range of techniques including vulnerability scanning, manual testing, and social engineering. The penetration tester attempts to gain access to the system, escalate privileges, and access sensitive data or functionality within the application. The testing can be performed from various perspectives, such as an external attacker or an insider threat, to identify vulnerabilities from different angles.
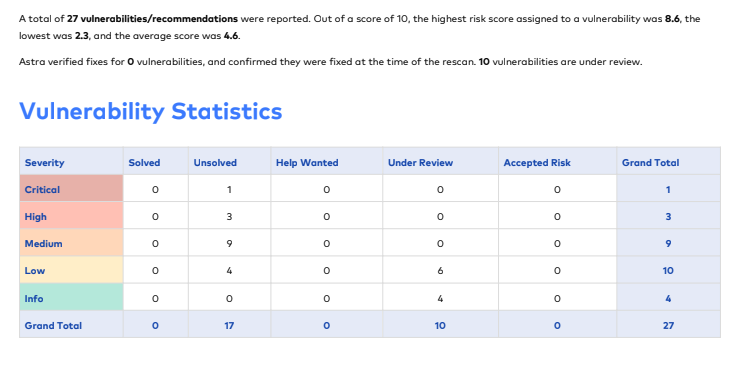
A Sample Manual Penetration Test Report
Continuous Pen Testing, Continuous Compliance
Through this work, we have been introducing the idea of implementing continuous, automated pen testing and vulnerability scanning, as a way to actively ensure there is no regression or new vulnerabilities exposed, and that any required compliance is maintained.
Automated cloud testing infrastructure can help you maintain “year-round compliance” for standards that include ISO, SOC2, GDPR, CIS, and HIPAA. It can also help you identity and address any new Common Vulnerabilities and Exposures (CVE) in “real-time” through continuous scans and regression testing.
See the Resourcessection for more information on specific tool and service recommendations.